Secure KVM switches
Posted on April 22, 2018 by KVMGalore | 0 comments
Secure KVM switches: Security threats against classified data

Using typical non secure KVM switches to access computers which belong to a mix of classified and non-classified networks poses the risk that the shared peripherals (via the KVM switch) might facilitate data-leaking between the computers.
Such data-leakage can make it easier for cyber-attackers to obtain classified information in their pursuit after their ultimate target - your secured network assets.
Electronic emissions may also pose a threat to secure environments as these stray signals provide a conduit by which sensitive information could easily leak into the wrong hands. Video cables, for example, can emit strong emissions that can be collected and duplicated to view the same image elsewhere.
Another threat includes power sources that can be used to conduct data back into a mains electricity supply and this in turn can be picked out using sensitive devices outside of the system's physical location.
The solution
Physical network segregation is considered one of the safest ways for obtaining the highest level of security. By creating secluded network islands it is possible to achieve real security and effectively segregate classified and non-classified computer environments.
Unintended consequences
Yet with the security benefits of network segregation come a usability issue. Users are forced to distribute their work between multiple computers that belong to multiple security-level networks. Working with multiple computers obstructs the convenience of the common single-computer work scenario. For that reason various peripheral sharing switch devices such as keyboard-mouse (KM) and keyboard-video-mouse (KVM) switches which allow the user to share a single mouse, keyboard, video and audio peripherals between multiple computers are commonly used in such environments.
The risk
The most vulnerable part of any network is the user access point. And when you use a KVM switch to access computers which belong to a mix of classified and non-classified networks, there is a risk that the shared peripherals (via the KVM switch) might facilitate data-leaking between the computers. The use of a centralized access-point (the KVM switch) to access such mix-environment computers also makes the KVM switch susceptible to physical hacking intended to gain access to classified data.
This makes traditional (non-secure) KM/KVM switches vulnerable. While offering centralized control of multiple computers, traditional non-secure KVM switches offer no absolute isolation between them. This exposes systems to the possibility of malicious damage, disruption, and acquisition of sensitive data from one computer to another, posing a significant security risk.
This is why federal, military, and intelligence agencies around the world have strict requirements regarding the security of KVM switches to safeguard data from accidental transfer or unauthorized access.
Resolution
The most effective way to mitigate any data leakage is to ensure that all data coming into and out of the KM/KVM switch is completely isolated. Add physical housing-intrusion detection an tamper-proof sealing to prevent physical hacking, and you have a secure KVM switch.
What is a secure KVM switch?
Secure KVM switches are designed from the ground up to obstacle threats derived from sharing peripheral devices utilizing a variety of mechanical, electrical and optical elements explicitly conceived to prevent unauthorized access, ensure signal isolation to accomplish secure data segregation, and prevent physical hacking into. Thus, secure KVM switches are optimized for accessing computers belonging to networks at different levels of security, especially useful for government, military, and defense operations.
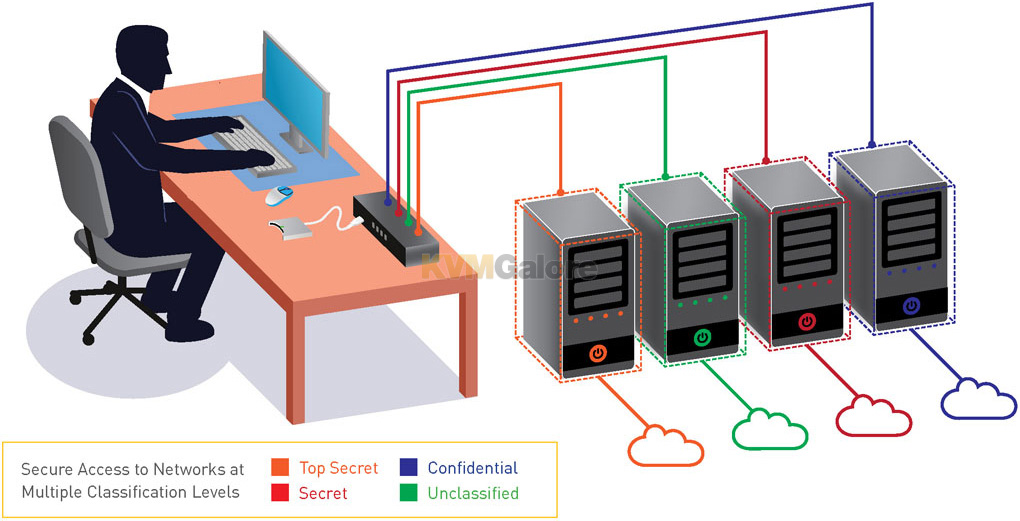
By enforcing multilayered security mechanisms, secure KVM switches are designed to block peripheral exploits, block information leaks, block eavesdropping, block signal transmission, and prevent computer malware, and hardware & firmware tampering.
Secure KVM switches prevent vulnerable peripherals from mediating between computers by isolating all hosts from each other and from the peripherals that are being shared through them, thus keeping the data of each computer completely separate.
Tools for verifying security claims for a secure KVM switch
 National Information Assurance Partnership (NIAP) is a program - officially known as the NIAP Common Criteria Evaluation and Validation Scheme for IT Security - established by he National Institute of Standards and Technology (NIST) and the National Security Agency (NSA) designed to evaluate IT product conformance to Common Criteria standard, and is responsible for U.S. implementation of the Common Criteria.
National Information Assurance Partnership (NIAP) is a program - officially known as the NIAP Common Criteria Evaluation and Validation Scheme for IT Security - established by he National Institute of Standards and Technology (NIST) and the National Security Agency (NSA) designed to evaluate IT product conformance to Common Criteria standard, and is responsible for U.S. implementation of the Common Criteria.
The program is being implemented to help consumers select commercial off-the-shelf information technology (IT) products that meet their security requirements and to help manufacturers of those products gain acceptance in the global marketplace.
Over the years, NIAP has come out with upgraded sets of requirements secure KVMs need to adhere to in order to be certified as secure KVM switches:
 PPs 4.0
PPs 4.0
The newest NIAP Common Criteria certificate for Protection Profile for Peripheral Sharing Switch Version 4.0, describing security requirements for a Peripheral Sharing Device (PSD), defined to provide a mechanism to securely connect a common set of peripherals to the attached computer(s), is intended to provide a minimal, baseline set of requirements that are targeted at mitigating well-defined and described threats. It represents an evolution of "traditional" Protection Profiles and the associated evaluation of the requirements contained within the document.
PPs 3.0
A NIAP Common Criteria certificate for Protection Profile for Peripheral Sharing Switch Version 3.0.
 PPs 3.0 brings an updated view which realizes that peripherals are vulnerable and can be used for abusing and penetrating secure environments. This updated threat perception acknowledges that peripherals and peripheral sharing is unsafe unless achieved through a highly secure peripheral sharing device.
PPs 3.0 brings an updated view which realizes that peripherals are vulnerable and can be used for abusing and penetrating secure environments. This updated threat perception acknowledges that peripherals and peripheral sharing is unsafe unless achieved through a highly secure peripheral sharing device.
EAL
EAL (Evaluation Assurance Level) is assigned a number based on the set of security testing criteria as classified by Common Criteria (CC). Each level has a unique rubric for testing security profiles involving function, structure, method, design, documentation, and/or use analysis.
The two main CC Assurance Level evaluations typically used for Secure KVM Switches are EAL 2 and EAL 4.
EAL 2: Structurally tested.
EAL 4: Methodically designed, tested and reviewed.
A higher EAL rating does not indicate a higher level of security. It simply indicates a more rigorous evaluation process.
TEMPEST certification
TEMPEST is a specification created by NSA and NATO for certifying IT systems against the possibility of spying through leaking emanations such as electrical signals, radio waves, sounds, and vibration. While most of TEMPEST covers electrical signal and radio wave emanation, it also stringently covers sound and mechanical vibration.
Many specifics of the TEMPEST standards are classified and therefore unavailable for public review. What we do know is TEMPEST protects equipment from eavesdropping by shielding, filtering, masking, and/or limiting the distance of transmissions.
Multilayered security features typically included in a secure KVM switch
Isolated data channels in each KVM port make it impossible for data to be transferred between connected computers through the KVM.
No-buffer design. Secure KVMs do not utilize a physical memory buffer, thus preventing any eavesdropping or key logging attempts. The keyboard and mouse USB buffers are automatically cleared after data transmission.
Restricted USB function only recognizes USB keyboards and mice to prevent inadvertent and insecure data transfer. Other USB devices, such as USB storage drives, are actively prohibited.
Locked firmware cannot be reprogrammed, preventing any attempts to alter the operation of the KVM.
Safe buffer design doesn't incorporate a memory buffer, and the keyboard buffer is automatically cleared after data transmission, preventing transfer of keystrokes or other data when switching between computers.
Tamper-proof hardware - all integrated circuits are soldered directly to the circuit board to prevent tampering with the components.
Push-button control requires physical access to KVM when switching between connected computers, prohibiting switching via the keyboard. Keyboard Hot Key shortcuts, automatic scanning, voice activation, and other switching methods requiring buffer are prohibited.
 Long-life internal anti-tampering battery.
Long-life internal anti-tampering battery.
Housing intrusion detection causes the KVM system to become inoperable and the LEDs to flash repeatedly if the housing has been opened.
Tamper-proof seals on the KVM chassis provide clear visual evidence if the enclosure has been opened or compromised.
CAC (Common Access Card) device support, such as smart-card and biometric readers for bolstering user authentication.
Do I need a secure KVM switch?
If you're looking to control multiple computers, with some or all of them containing classified data (or belonging to classified networks) - you want to deploy a secure KVM switch.
Which secure KVM switch to choose?
Look for a secure KVM switch that has been certified. All levels of certification translate into a promise that the certified secure KVM switch is indeed secure. Nevertheless, it is acceptable in the marketplace that the available certifications are ranked in the following order (1st in list considered the 'best'):
1. PPs 4.0
2. PPs 3.0
3. EAL 4
4. EAL 2
5. TEMPEST
Which brand to choose?
For a variety of reasons, including product availability, certification level, original manufacturing and the age of their technology, KVMGalore is recommending secure KVM switches made by Adder, ATEN, IOGEAR, iPGARD, Sekuryx and Vertiv-Cybex, with iPGARD currently offering the widest selection of models.
Need help? Call KVMGalore at 1-800-636-3434 or submit your question.






